Page 52 - CITS - Computer Software Application -TT
P. 52
COMPUTER SOFTWARE APPLICATION - CITS
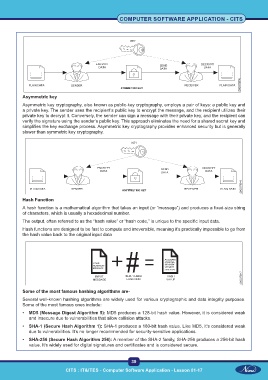
Asymmetric key
Asymmetric key cryptography, also known as public-key cryptography, employs a pair of keys: a public key and
a private key. The sender uses the recipient’s public key to encrypt the message, and the recipient utilizes their
private key to decrypt it. Conversely, the sender can sign a message with their private key, and the recipient can
verify the signature using the sender’s public key. This approach eliminates the need for a shared secret key and
simplifies the key exchange process. Asymmetric key cryptography provides enhanced security but is generally
slower than symmetric key cryptography.
Hash Function
A hash function is a mathematical algorithm that takes an input (or “message”) and produces a fixed-size string
of characters, which is usually a hexadecimal number.
The output, often referred to as the “hash value” or “hash code,” is unique to the specific input data.
Hash functions are designed to be fast to compute and irreversible, meaning it’s practically impossible to go from
the hash value back to the original input data
Some of the most famous hashing algorithms are-
Several well-known hashing algorithms are widely used for various cryptographic and data integrity purposes.
Some of the most famous ones include:
• MD5 (Message Digest Algorithm 5): MD5 produces a 128-bit hash value. However, it is considered weak
and insecure due to vulnerabilities that allow collision attacks.
• SHA-1 (Secure Hash Algorithm 1): SHA-1 produces a 160-bit hash value. Like MD5, it’s considered weak
due to vulnerabilities. It’s no longer recommended for security-sensitive applications.
• SHA-256 (Secure Hash Algorithm 256): A member of the SHA-2 family, SHA-256 produces a 256-bit hash
value. It’s widely used for digital signatures and certificates and is considered secure.
39
CITS : IT&ITES - Computer Software Application - Lesson 01-17