Page 13 - Computer Software Application TP - Volume 1
P. 13
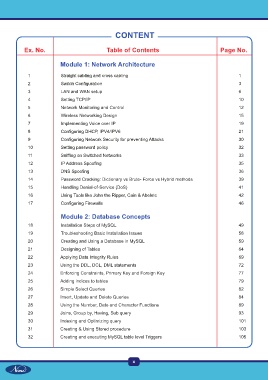
CONTENT
Ex. No. Table of Contents Page No.
Module 1: Network Architecture
1 Straight cabling and cross cabling 1
2 Switch Configuration 3
3 LAN and WAN setup 6
4 Setting TCP/IP 10
5 Network Monitoring and Control 12
6 Wireless Networking Design 15
7 Implementing Voice over IP 19
8 Configuring DHCP, IPV4/IPV6 21
9 Configuring Network Security for preventing Attacks 30
10 Setting password policy 32
11 Sniffing on Switched Networks 33
12 IP Address Spoofing 35
13 DNS Spoofing 3 6
14 Password Cracking: Dictionary vs Brute- Force vs Hybrid methods 39
15 Handling Denial-of-Service (DoS) 41
16 Using Tools like John the Ripper, Cain & Abeletc 42
17 Configuring Firewalls 46
Module 2: Database Concepts
18 Installation Steps of MySQL 49
19 Troubleshooting Basic Installation Issues 58
20 Creating and Using a Database in MySQL 59
21 Designing of Tables 64
22 Applying Data Integrity Rules 69
23 Using the DDL, DCL, DML statements 72
24 Enforcing Constraints, Primary Key and Foreign Key 77
25 Adding indices to tables 79
26 Simple Select Queries 82
27 Insert, Update and Delete Queries 84
28 Using the Number, Date and Character Functions 89
29 Joins, Group by, Having, Sub query 93
30 Indexing and Optimizing query 101
31 Creating & Using Stored procedure 103
32 Creating and executing MySQL table level Triggers 105
x