Page 21 - CITS - Computer Software Application -TT
P. 21
COMPUTER SOFTWARE APPLICATION - CITS
• Scalability: You can easily expand the network by adding more devices or ports to the central hub as needed.
• Fault Isolation: If one device or cable fails, it doesn’t affect the rest of the network. Only the malfunctioning
device or cable needs to be addressed.
Disadvantages of a Star Topology:
• Single Point of Failure: If the central hub or switch fails, the entire network may become inaccessible.
Redundancy measures can mitigate this risk.
• Cost: Setting up a star topology can be more expensive than some other topologies, as it requires a central
hub with enough ports for all devices.
• Cable Length: The maximum cable length between a device and the central hub is limited, which may be a
constraint in large networks.
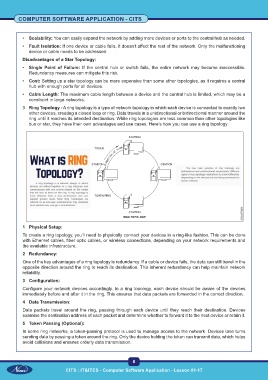
3 Ring Topology - A ring topology is a type of network topology in which each device is connected to exactly two
other devices, creating a closed loop or ring. Data travels in a unidirectional or bidirectional manner around the
ring until it reaches its intended destination. While ring topologies are less common than other topologies like
bus or star, they have their own advantages and use cases. Here’s how you can use a ring topology:
1 Physical Setup:
To create a ring topology, you’ll need to physically connect your devices in a ring-like fashion. This can be done
with Ethernet cables, fiber optic cables, or wireless connections, depending on your network requirements and
the available infrastructure.
2 Redundancy:
One of the key advantages of a ring topology is redundancy. If a cable or device fails, the data can still travel in the
opposite direction around the ring to reach its destination. This inherent redundancy can help maintain network
reliability.
3 Configuration:
Configure your network devices accordingly. In a ring topology, each device should be aware of the devices
immediately before and after it in the ring. This ensures that data packets are forwarded in the correct direction.
4 Data Transmission:
Data packets travel around the ring, passing through each device until they reach their destination. Devices
examine the destination address of each packet and determine whether to forward it to the next device or retain it.
5 Token Passing (Optional):
In some ring networks, a token-passing protocol is used to manage access to the network. Devices take turns
sending data by passing a token around the ring. Only the device holding the token can transmit data, which helps
avoid collisions and ensures orderly data transmission.
8
CITS : IT&ITES - Computer Software Application - Lesson 01-17