Page 43 - CITS - Computer Software Application -TT
P. 43
COMPUTER SOFTWARE APPLICATION - CITS
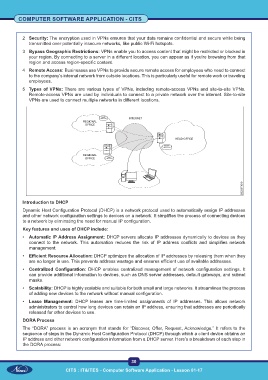
2 Security: The encryption used in VPNs ensures that your data remains confidential and secure while being
transmitted over potentially insecure networks, like public Wi-Fi hotspots.
3 Bypass Geographic Restrictions: VPNs enable you to access content that might be restricted or blocked in
your region. By connecting to a server in a different location, you can appear as if you’re browsing from that
region and access region-specific content.
4 Remote Access: Businesses use VPNs to provide secure remote access for employees who need to connect
to the company’s internal network from outside locations. This is particularly useful for remote work or traveling
employees.
5 Types of VPNs: There are various types of VPNs, including remote-access VPNs and site-to-site VPNs.
Remote-access VPNs are used by individuals to connect to a private network over the internet. Site-to-site
VPNs are used to connect multiple networks in different locations.
Introduction to DHCP
Dynamic Host Configuration Protocol (DHCP) is a network protocol used to automatically assign IP addresses
and other network configuration settings to devices on a network. It simplifies the process of connecting devices
to a network by eliminating the need for manual IP configuration.
Key features and uses of DHCP include:
• Automatic IP Address Assignment: DHCP servers allocate IP addresses dynamically to devices as they
connect to the network. This automation reduces the risk of IP address conflicts and simplifies network
management.
• Efficient Resource Allocation: DHCP optimizes the allocation of IP addresses by releasing them when they
are no longer in use. This prevents address wastage and ensures efficient use of available addresses.
• Centralized Configuration: DHCP enables centralized management of network configuration settings. It
can provide additional information to devices, such as DNS server addresses, default gateways, and subnet
masks.
• Scalability: DHCP is highly scalable and suitable for both small and large networks. It streamlines the process
of adding new devices to the network without manual configuration.
• Lease Management: DHCP leases are time-limited assignments of IP addresses. This allows network
administrators to control how long devices can retain an IP address, ensuring that addresses are periodically
released for other devices to use.
DORA Process
The “DORA” process is an acronym that stands for “Discover, Offer, Request, Acknowledge.” It refers to the
sequence of steps in the Dynamic Host Configuration Protocol (DHCP) through which a client device obtains an
IP address and other network configuration information from a DHCP server. Here’s a breakdown of each step in
the DORA process:
30
CITS : IT&ITES - Computer Software Application - Lesson 01-17