Page 81 - CITS - Computer Software Application -TT
P. 81
COMPUTER SOFTWARE APPLICATION - CITS
Example
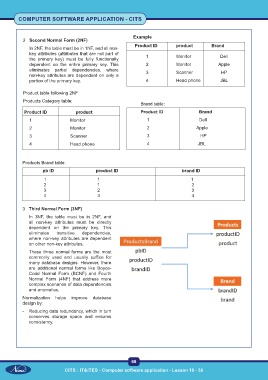
2 Second Normal Form (2NF)
Product ID product Brand
In 2NF, the table must be in 1NF, and all non-
key attributes (attributes that are not part of 1 Monitor Dell
the primary key) must be fully functionally
dependent on the entire primary key. This 2 Monitor Apple
eliminates partial dependencies, where 3 Scanner HP
non-key attributes are dependent on only a
portion of the primary key. 4 Head phone JBL
Product table following 2NF
Products Category table:
Brand table:
Product ID product Product ID Brand
1 Monitor 1 Dell
2 Monitor 2 Apple
3 Scanner 3 HP
4 Head phone 4 JBL
Products Brand table:
pb ID product ID brand ID
1 1 1
2 1 2
3 2 3
4 3 4
3 Third Normal Form (3NF)
In 3NF, the table must be in 2NF, and
all non-key attributes must be directly
dependent on the primary key. This
eliminates transitive dependencies,
where non-key attributes are dependent
on other non-key attributes.
These three normal forms are the most
commonly used and usually suffice for
many database designs. However, there
are additional normal forms like Boyce-
Codd Normal Form (BCNF) and Fourth
Normal Form (4NF) that address more
complex scenarios of data dependencies
and anomalies.
Normalization helps improve database
design by:
- Reducing data redundancy, which in turn
conserves storage space and ensures
consistency.
68
CITS : IT&ITES - Computer software application - Lesson 18 - 36