Page 84 - CITS - Computer Software Application -TT
P. 84
COMPUTER SOFTWARE APPLICATION - CITS
to each table entry. These primary keys serve the purpose of uniquely identifying each record in the table, even
in cases where other attributes like name and age might not be sufficient for differentiation.
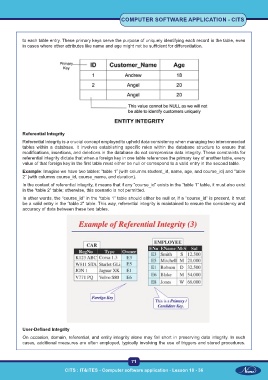
Referential Integrity
Referential Integrity is a crucial concept employed to uphold data consistency when managing two interconnected
tables within a database. It involves establishing specific rules within the database structure to ensure that
modifications, insertions, and deletions in the database do not compromise data integrity. These constraints for
referential integrity dictate that when a foreign key in one table references the primary key of another table, every
value of that foreign key in the first table must either be null or correspond to a valid entry in the second table.
Example: Imagine we have two tables: “table 1” (with columns student_id, name, age, and course_id) and “table
2” (with columns course_id, course_name, and duration).
In the context of referential integrity, it means that if any “course_id” exists in the “table 1” table, it must also exist
in the “table 2” table; otherwise, this scenario is not permitted.
In other words, the “course_id” in the “table 1” table should either be null or, if a “course_id” is present, it must
be a valid entry in the “table 2” table. This way, referential integrity is maintained to ensure the consistency and
accuracy of data between these two tables.
User-Defined Integrity
On occasion, domain, referential, and entity integrity alone may fall short in preserving data integrity. In such
cases, additional measures are often employed, typically involving the use of triggers and stored procedures.
71
CITS : IT&ITES - Computer software application - Lesson 18 - 36