Page 28 - CITS - Computer Software Application -TT
P. 28
COMPUTER SOFTWARE APPLICATION - CITS
• Robustness: If a link or node in the network fails, packet-switched networks can often reroute packets through
alternative paths, making them more resilient to network failures.
• Scalability: Packet switching is highly scalable, making it suitable for networks of various sizes, from small
local area networks (LANs) to global-scale networks like the internet.
• Common Protocols: Common networking protocols that use packet switching include the Internet Protocol
(IP) for the internet and Ethernet for LANs.
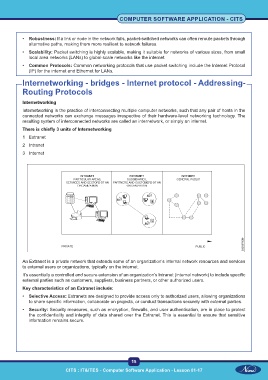
Internetworking - bridges - Internet protocol - Addressing-
Routing Protocols
Internetworking
Internetworking is the practice of interconnecting multiple computer networks, such that any pair of hosts in the
connected networks can exchange messages irrespective of their hardware-level networking technology. The
resulting system of interconnected networks are called an internetwork, or simply an internet.
There is chiefly 3 units of Internetworking
1 Extranet
2 Intranet
3 Internet
An Extranet is a private network that extends some of an organization’s internal network resources and services
to external users or organizations, typically on the internet.
It’s essentially a controlled and secure extension of an organization’s Intranet (internal network) to include specific
external parties such as customers, suppliers, business partners, or other authorized users.
Key characteristics of an Extranet include:
• Selective Access: Extranets are designed to provide access only to authorized users, allowing organizations
to share specific information, collaborate on projects, or conduct transactions securely with external parties.
• Security: Security measures, such as encryption, firewalls, and user authentication, are in place to protect
the confidentiality and integrity of data shared over the Extranet. This is essential to ensure that sensitive
information remains secure.
15
CITS : IT&ITES - Computer Software Application - Lesson 01-17